A recent attack on the Kenyan government's E-citizen platform is a clear reminder of the importance of robust infrastructure. Had the attack succeeded, it could have led to a massive data breach, costing the government millions of dollars and causing economic turmoil.
Therefore, choosing the right product goes beyond price, aesthetics, and functionality. It is crucial to prioritise the security aspect of a tool, especially with the increasing rate of digitisation and cyber-attacks across Africa, posing a significant threat to businesses and individuals alike.
African Business reports that a significant number of African businesses, approximately 90%, operate without adequate cybersecurity infrastructure, leaving them increasingly vulnerable to cyber threats like hacking, phishing, and malware attacks, which are common methods employed by cybercriminals to steal valuable data. In the current landscape, where data has become an invaluable asset for organisations, it is crucial to prioritise the selection of tools that can help mitigate these risks and prevent such incidents.
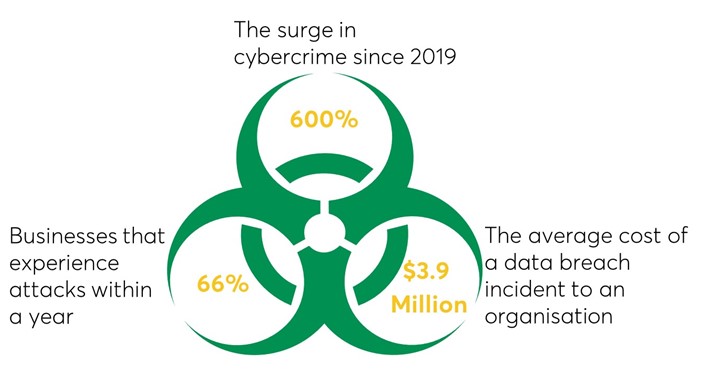
The numbers below highlight the urgency of prioritising product security:
So, how can one identify secure tools and software you ask? Here are some key factors to consider:
Privacy Policy: A comprehensive policy should include consent and control, security measures in place, data sharing and third parties and compliance with laws and regulations among others: Take the time to read and understand the privacy policy of any tool you're considering. Ensure they prioritise the protection and confidentiality of your data.
Multi-Factor Authentication: Look for tools that offer multiple layers of authentication to prevent unauthorised access.
Permission Requests: Pay attention to the permissions a tool requests. Make sure they align with the features and functionalities it provides. If they ask for unnecessary access to your personal information, it's a red flag. Look for tools that provide granular permission settings, allowing you to control access to sensitive data.
Encryption and Data Protection: Tools that utilise encryption and robust data protection measures are essential for keeping your information safe from prying eyes. A user can know this by reading the product documentation, looking for independent reviews and evaluations, and checking if the product has undergone any security certifications or audits among others.
Regular Updates:Choose products that receive frequent updates and security patches, to address vulnerabilities, keeping them resilient against emerging threats.
Support and Responsiveness: Opt for tools that offer reliable customer support and demonstrate a commitment to promptly addressing security concernsand audits among others.
Remember, even the most secure tools are only as good as their users. Stay informed about the latest tactics used by attackers and adopt safe data protection practices. Regularly update software, use strong passwords, be cautious of suspicious emails or links, and practice secure browsing habits.
References.
Morgan, S. (2020). Cybercrime to cost the world $10.5 trillion annually by 2025. Retrieved from Cybercrime Magazine: https://cybersecurityventures.com/hackerpocalypse-cybercrime-report-2016/
Mclean, M. (2023). 2023 must-know cyber-attack statistics and trends. Retrieved from Embroker: https://www.embroker.com/blog/cyber-attack-statistics/
Komminoth, Leo. (2023). Africa’s cyber-security threat. Retrieved from Africa Business: https://african.business/2023/02/technology-information/africas-cybersecurity-threat





